
With over 3 years of crypto writing experience, Bena strives to make crypto, blockchain, Web3, and fintech accessible to all. Beyond cryptocurrencies, Bena also enjoys reading books in her spare time.
A major disruption targeting the LockBit ransomware group, combined with increased law enforcement actions, led to a significant 79% drop in ransomware payments during the second half of 2024.
 Edited by Marco T. Lanz
Updated
4 mins read
Edited by Marco T. Lanz
Updated
4 mins read

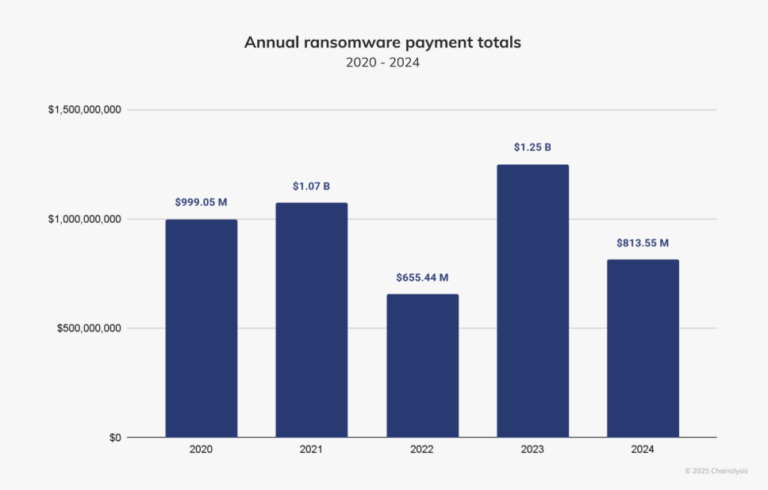
Global ransomware extortion payments plunged 35% in 2024, dropping to $813 million from the record-breaking $1.25 billion seen in 2023, according to blockchain analytics firm Chainalysis. The decline followed aggressive crackdowns on illicit crypto exchanges and a growing number of victims refusing to pay.
Source: Chainalysis
Between January and June, attackers extorted $459.8 million, reflecting a modest 2.38% rise from the first half of 2023. However, the latter half of the year saw a sharp reversal, with payments falling by nearly 35%. The most notable outlier was a $75 million ransom paid to the cybercriminal group Dark Angels.
“This slowdown is similar to the HoH decline in ransom payments since 2021 and the overall decline during H2 2024 in some types of crypto-related crime, such as stolen funds. Notably, the decline this year is more pronounced than in the last three years,” said Chainalysis.
Law enforcement actions played a critical role in the downturn. A major disruption targeted LockBit, once a dominant ransomware strain, leading to a staggering 79% drop in payments during the year’s second half. A joint operation between the UK’s National Crime Agency (NCA) and the US FBI dismantled parts of the group’s infrastructure, severely limiting its operations.
LockBit’s decline, along with the collapse of BlackCat/ALPHV in January 2024, created a power vacuum in the ransomware landscape. Smaller groups attempted to seize control, but none matched the scale of their predecessors. RansomHub, however, quickly rose to prominence, absorbing many displaced cybercriminals. Despite launching in February, it became the most active ransomware strain by victim count, securing a spot among the top 10 extortion groups of the year.
Source: Chainalysis
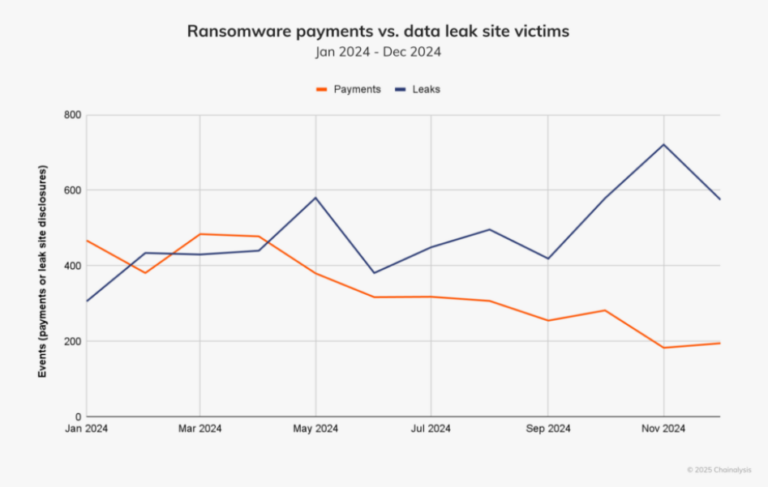
New players also emerged on the data leak front. 56 fresh data leak sites appeared in 2024, more than double the previous year’s number. However, many of these were deceptive—over 100 victims were listed multiple times across different platforms, and LockBit falsely claimed up to 68% of its listed victims. Cybercriminals exaggerated their reach to maintain relevance despite increased enforcement pressure.
Even as new threats surfaced, victims grew more resistant to paying. The latter half of the year saw a 53% gap between ransom demands and actual payments. Only 30% of negotiations resulted in payments, a stark contrast to previous years. More companies opted for backups, decryption tools, or other recovery methods instead of giving in to extortion.
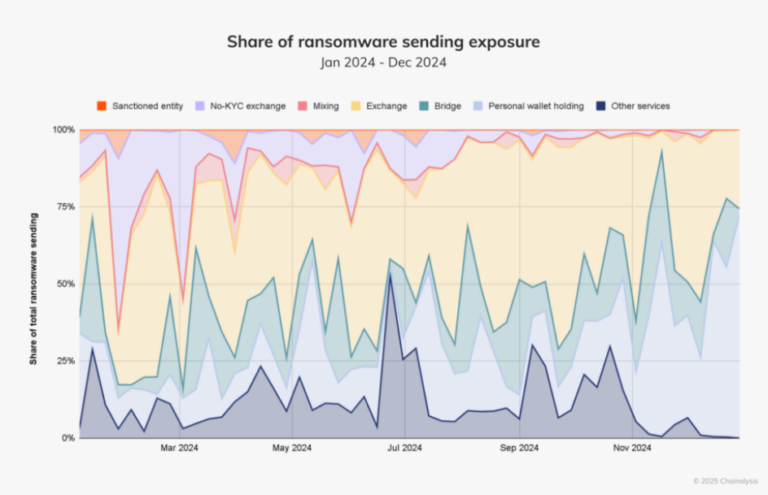
With enforcement ramping up, cybercriminals found it increasingly difficult to launder extorted funds. Centralized exchanges processed 39% of ransomware proceeds in 2024, slightly above the four-year average of 37%. However, the use of crypto mixers—once a popular laundering tool—dropped sharply due to actions against platforms like Chipmixer, Tornado Cash, and Sinbad.
Source: Chainalysis
“Curiously, ransomware operators, a primarily financially motivated group, are abstaining from cashing out more than ever. We attribute this largely to increased caution and uncertainty amid what is probably perceived as law enforcement’s unpredictable and decisive actions targeting individuals and services participating in or facilitating ransomware laundering, resulting in insecurity among threat actors about where they can safely put their funds,” the report said.
No-KYC crypto exchanges, a favored channel for laundering illicit funds, also took a hit. A major law enforcement operation in September 2024 saw German authorities seize 47 Russian-language exchanges operating without Know-Your-Customer (KYC) requirements. The crackdown significantly reduced ransomware-related inflows to these platforms, forcing cybercriminals to explore alternative laundering methods.
Further tightening the net on ransomware actors, Israeli-Russian citizen Rostislav Panev was arrested for developing tools used by LockBit and receiving approximately $230,000 in Bitcoin. His capture further crippled LockBit’s attempted resurgence and highlighted the growing effectiveness of blockchain-based law enforcement investigations.
Disclaimer: Coinspeaker is committed to providing unbiased and transparent reporting. This article aims to deliver accurate and timely information but should not be taken as financial or investment advice. Since market conditions can change rapidly, we encourage you to verify information on your own and consult with a professional before making any decisions based on this content.

With over 3 years of crypto writing experience, Bena strives to make crypto, blockchain, Web3, and fintech accessible to all. Beyond cryptocurrencies, Bena also enjoys reading books in her spare time.





